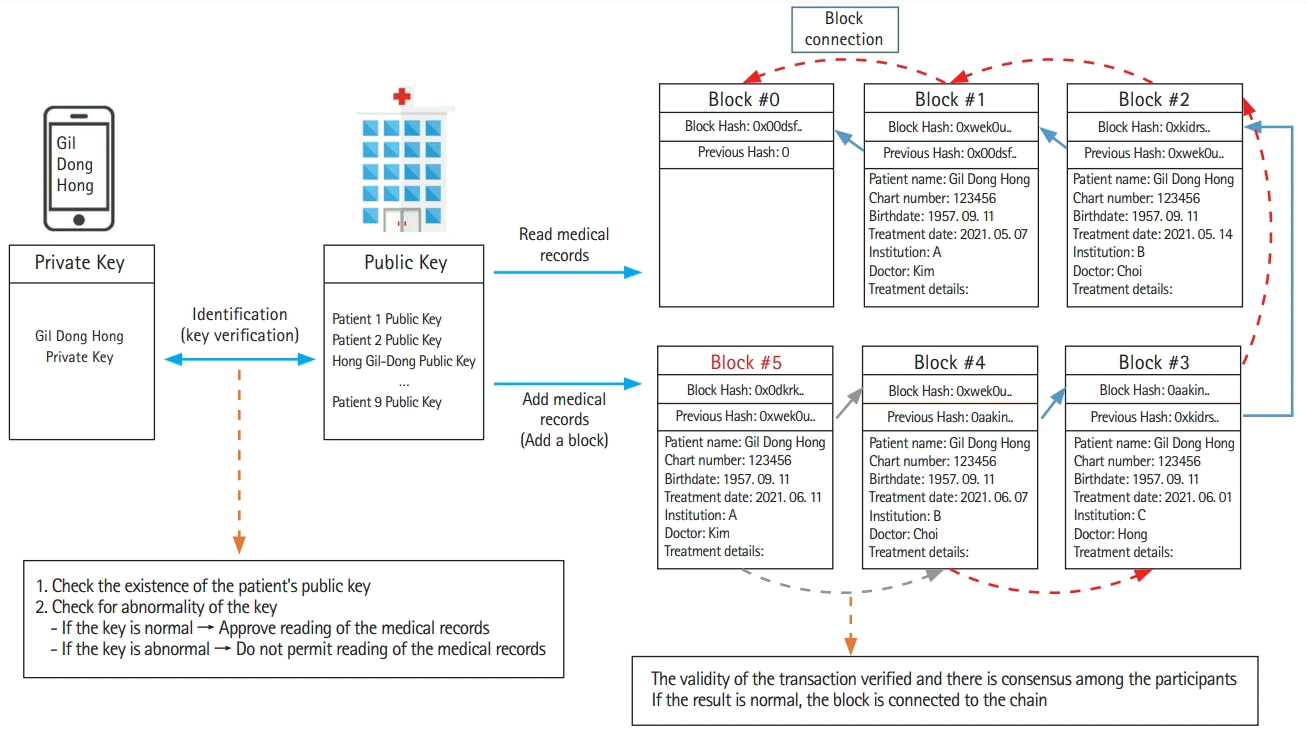
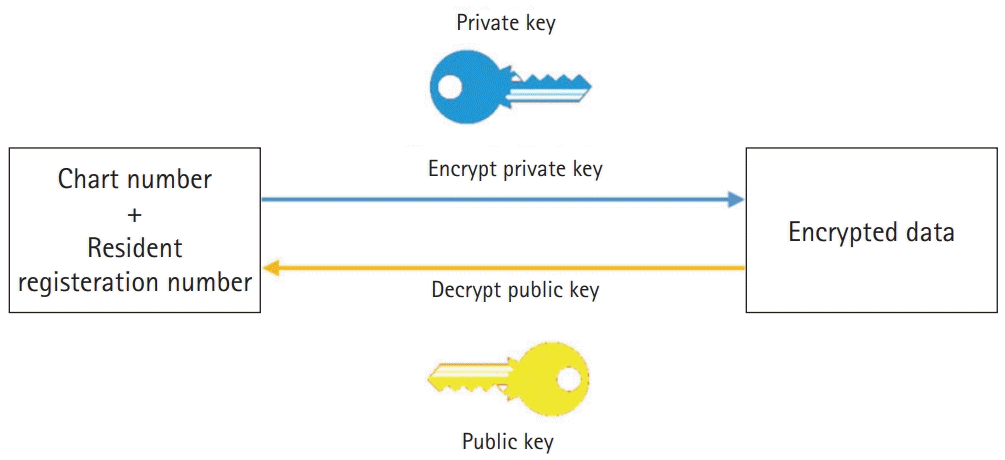
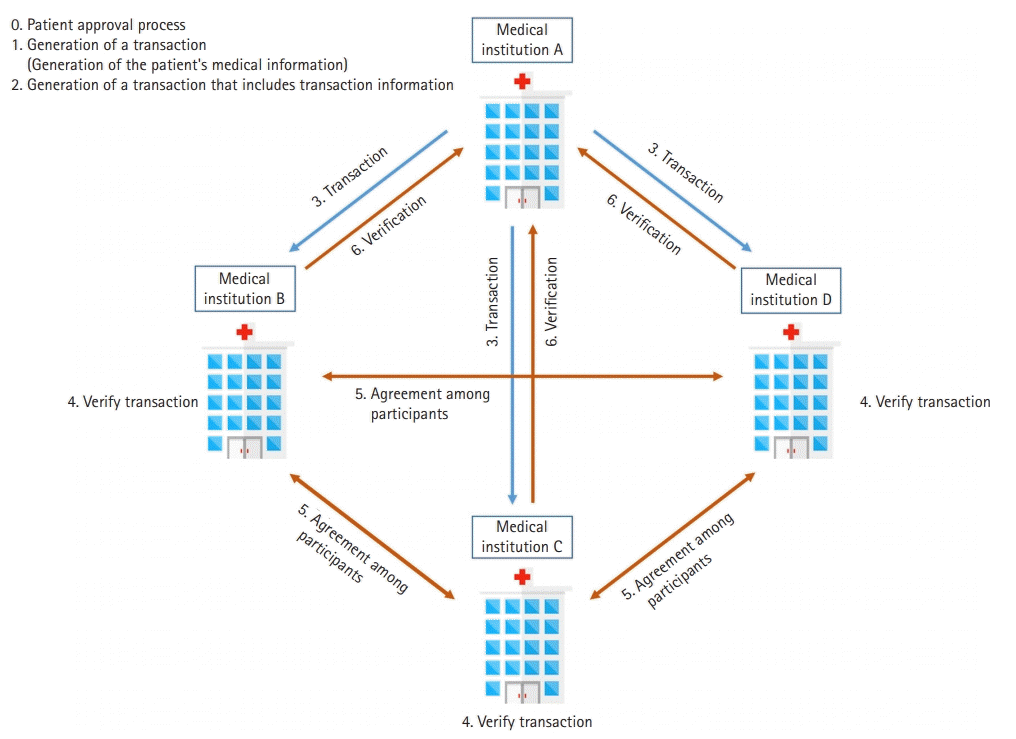
Whenever a transaction of medical information is performed, a block that contains the transaction information is generated and connected continuously to other blocks, and the information is stored in a distributed manner at the medical institutions participating in the network. Many blocks are closely interconnected through the hash values. A hash value is data that is converted to a special text string of a fixed length in which the original data cannot be distinguished when the hash goes through the hash function. The transaction information is reflected in the hash value of the newly generated block. When the internal data of a specific block in the blockchain changes, the hash value automatically changes, which also affects other blocks. In this way, a blockchain allows data tampering to be easily detected. In the blockchain, the hash value is used to add the corresponding block to the chain, and the hash value of the previous block is recorded in the current block. As a result, a connected list is created in the form of chain. Therefore, in order to hack a specific block, it is necessary to tamper with other blocks connected to the block of interest, making forgery exceedingly difficult.
To create a block object, a verified transaction is added to the chain, and the transaction information is reflected in the hash value of the block. A new block hash is then generated using the previous block hash. The hash value of the previous block is saved in the newly generated block that follows it.
Generation of blockchain lists using hash values that reflect transaction information
block = new Block(block.getBlockID()+1, block.getBlockHash(), Util.getDate(), patientsData, new ArrayList<Transaction>());
// A transaction is generated to add to the medical record of patient 2673123.
transaction = new Transaction(key, patientsData.getPatientsData());
block.addTransaction(transaction);
// The transaction information is reflected in the hash value of the block.
// If the transaction information in a block is changed, the hash values of all subsequent blocks are also changed.
public String getBlockHash() {
// The block hash is created using the previous block hash.
return Util.getHash(getTransaction() + previousBlockHash);
}
// The SHA-256 hash value, which is returned as a text string, passes through the function.
// When the value of the text string changes, the hash value also changes.
// For the SHA-256 hash algorithm, the Avalanche Effect method is applied.
public static String getHash(String input) {
StringBuffer result = new StringBuffer();
try {
MessageDigest md = MessageDigest.getInstance("SHA-256");
md.update(input.getBytes());
byte bytes[] = md.digest();
for(int i=0;i<bytes.lengthi++) {
result.append(Integer.toString((bytes[i] & 0xff) + 0x100, 16).substring(1));
}
} catch(Exception e) {
e.printStackTrace();
}
return result.toString();
}
SHA, secure hash algorithm.
The patient’s medical information is stored in the generated block, and multiple blocks form a list that is connected through their hash values.
Blockchain list information
=============================================================================
Block number: 0
Created time: 2021-06-14 01:51:36.640
Previous hash: null
Block hash: 74234e98afe7498fb5daf1f36ac2d78acc339464f950703b8c019892f982b90b
Medical record:
=============================================================================
A normal transaction was found.
=============================================================================
Block number: 1
Created time: 2021-06-14 01:51:39.661
Previous hash: 74234e98afe7498fb5daf1f36ac2d78acc339464f950703b8c019892f982b90b
Block hash: 6345e8d4fe0b749dfe1862cbfd90817f38dd3692cd2cd918be58e5becd540944
Medical record:
NAME: Gil Dong Hong
AGE: 50
GENDER: M
STROKE: Lt. hemiplegia d/t Rt. CR infarct
ONSET: Jan/01/2021
MEP: Jan/12/2021: Rt. ABP 20.6/5600, Lt. ABP NR; Rt. TA 19.5/2200, Lt. TA NR
SEP: Jan/12/2021 Rt. Median 19.0/24.2, Lt. Median NR; Rt. PT 38.2/45.0, Lt. PT NR
Evaluation data: Jan/10/2021
Bathel index: 30
MMSE: 24
GDS: 2
MVPT: 30
MFT: .30/8
Purdue: 16/NT
Grip Power: .50/6
Monofilament: 3.22/5.22
Two point discrimination: .4/6
Shoulder abductor: 1
Elbow flexor: 2
Finger flexor: 2
Finger extensor: 1
Hip flexor: 2
Knee extensor: 2
Ankle D/F: 1
FAC: 1
Aphasia type: conduction aphasia
AQ: 55
LQ: 48
Light tough: .20/12
Kinesthetic: .20/12
MBC: 2
GCS: 15
=============================================================================
A normal transaction was found.
=============================================================================
Block number: 2
Created time: 2021-06-14 01:51:42.704
Previous hash: 6345e8d4fe0b749dfe1862cbfd90817f38dd3692cd2cd918be58e5becd540944
Block hash: dbf72d6bf7143b6272308fb0708291c10733c0787553355753fb90e477113a7e
Medical record:
NAME: Gil Dong Hong
AGE: 50
GENDER: M
STROKE: Lt. hemiplegia d/t Rt. CR infarct
ONSET: Jan/01/2021
MEP: Jan/12/2021: Rt. ABP 20.6/5600, Lt. ABP NR; Rt. TA 19.5/2200, Lt. TA NR
SEP: Jan/12/2021 Rt. Median 19.0/24.2, Lt. Median NR; Rt. PT 38.2/45.0, Lt. PT NR
Evaluation data: Feb/10/2021
Bathel index: 52
MMSE: 27
GDS: 2
MVPT: 36
MFT: .30/10
Purdue: 16/NT
Grip Power: .50/8
Monofilament: 3.22/5.18
Two point discrimination: .4/6
Shoulder abductor: 2
Elbow flexor: 3
Finger flexor: 3
Finger extensor: 1
Hip flexor: 3
Knee extensor: 3
Ankle D/F: 1
FAC: 2
Aphasia type: conduction aphasia
AQ: 58
LQ: 52
Light tough: .20/14
Kinesthetic: .20/14
MBC: 3
GCS: 15
=============================================================================
A normal transaction was found.
=============================================================================
Block number: 3
Created time: 2021-06-14 01:51:45.737
Previous hash: dbf72d6bf7143b6272308fb0708291c10733c0787553355753fb90e477113a7e
Block hash: f55e598438047feeafac137016eda953396244cfffe148730499727203e72733
Medical record:
NAME: Gil Dong Hong
AGE: 50
GENDER: M
STROKE: Lt. hemiplegia d/t Rt. CR infarct
ONSET: Jan/01/2021
MEP: Jan/12/2021: Rt. ABP 20.6/5600, Lt. ABP NR; Rt. TA 19.5/2200, Lt. TA NR
SEP: Jan/12/2021 Rt. Median 19.0/24.2, Lt. Median NR; Rt. PT 38.2/45.0, Lt. PT NR
Evaluation data: Mar/13/2021
Bathel index: 58
MMSE: 28
GDS: 2
MVPT: 38
MFT: .30/12
Purdue: 16/NT
Grip Power: .50/8
Monofilament: 3.22/5.14
Two point discrimination: .4/6
Shoulder abductor: 3
Elbow flexor: 4
Finger flexor: 4
Finger extensor: 2
Hip flexor: 3
Knee extensor: 3
Ankle D/F: 2
FAC: 3
Aphasia type: conduction aphasia
AQ: 58
LQ: 54
Light tough: .20/16
Kinesthetic: .20/16
MBC: 4
GCS: 15
=============================================================================
A normal transaction was found.
=============================================================================
Block number: 4
Created time: 2021-06-14 01:51:48.754
Previous hash: f55e598438047feeafac137016eda953396244cfffe148730499727203e72733
Block hash: 5fdfbc0a7d30f454dfc24975805e353ca5912b4d81c9875447e6a99644650a8f
Medical record:
NAME: Gil Dong Hong
AGE: 50
GENDER: M
STROKE: Lt. hemiplegia d/t Rt. CR infarct
ONSET: Jan/01/2021
MEP: Jan/12/2021: Rt. ABP 20.6/5600, Lt. ABP NR; Rt. TA 19.5/2200, Lt. TA NR
SEP: Jan/12/2021 Rt. Median 19.0/24.2, Lt. Median NR; Rt. PT 38.2/45.0, Lt. PT NR
Evaluation data: May/01/2021
Bathel index: 60
MMSE: 28
GDS: 2
MVPT: 40
MFT: .30/12
Purdue: 16/NT
Grip Power: .50/8
Monofilament: 3.22/5.14
Two point discrimination: .4/6
Shoulder abductor: 3
Elbow flexor: 4
Finger flexor: 4
Finger extensor: 2
Hip flexor: 3
Knee extensor: 3
Ankle D/F: 2
FAC: 4
Aphasia type: conduction aphasia
AQ: 58
LQ: 56
Light tough: .20/16
Kinesthetic: .20/16
MBC: 4
GCS: 15
=============================================================================
MEP, motor evoked potential; ABP, abductor pollicis brevis; Rt, right; Lt, left; TA, tibialis anterior; PT, posterior tibial; NR, no response; SEP, sensory evoked potential; MMSE, mini-mental state examination; GDS, global deterioration scale; MVPT, motor-free visual perception test; MFT, manual function test; NT, not testable; D/F, dorsiflexor; FAC, functional ambulatory category; AQ, aphasia quotient; LQ, language quotient; MBC, modified Brunnstrom Classification; GCS, Glasgow Coma Scale.




 PDF
PDF Citation
Citation Print
Print

 XML Download
XML Download