1. Miller DP Jr, Latulipe C, Melius KA, Quandt SA, Arcury TA. Primary care providers’ views of patient portals: interview study of perceived benefits and consequences. J Med Internet Res. 2016; 18(1):e8.

2. Nausheen F, Begum SH. Healthcare IoT: benefits, vulnerabilities and solutions. In : Proceedings of 2018, 2nd International Conference on Inventive Systems and Control (ICISC) ; 2017 Jan 19ȓ20; Coimbatore, India. p. 517–22.

5. Lallie HS, Shepherd LA, Nurse JR, Erola A, Epiphaniou G, Maple C, et al. Cyber security in the age of COVID-19: a timeline and analysis of cyber-crime and cyberattacks during the pandemic. Computers & Security. 2021; 105:102248.

6. Muthuppalaniappan M, Stevenson K. Healthcare cyberattacks and the COVID-19 pandemic: an urgent threat to global health. Int J Qual Health Care. 2021; 33(1):mzaa117..

8. Tully J, Selzer J, Phillips JP, O’Connor P, Dameff C. Healthcare challenges in the era of cybersecurity. Health Secur. 2020; 18(3):228–31.

9. Evans D, Kolesnikov V, Rosulek M. A pragmatic introduction to secure multi-party computation. Found Trends Priv Secur. 2018; 2(2–3):70–246.

10. Gentry C. A fully homomorphic encryption scheme [dissertation]. Stanford (CA): Stanford University;2009.
11. Brakerski Z, Gentry C, Vaikuntanathan V. (Leveled) fully homomorphic encryption without bootstrapping. ACM Trans Comput Theory. 2014; 6(3):1–36.

12. Fan J, Vercauteren F. Somewhat practical fully homomorphic encryption [Internet]. Bellevue (WA): Cryptology ePrint Archive;2012. [cited at 2022 Mar 30]. Available from:
https://eprint.iacr.org/2012/144
.
13. Cheon JH, Kim A, Kim M, Song Y. Homomorphic encryption for arithmetic of approximate numbers. Takagi T, Peyrin T, editors. Advances in Cryptology – ASIACRYPT. 2017. Cham, Switzerland: Springer;2017. p. 409–37.

14. Alami H, Gagnon MP, Ahmed MA, Fortin JP. Digital health: cybersecurity is a value creation lever, not only a source of expenditure. Health Policy Technol. 2019; 8(4):319–21.

15. Alqarni A. Exploring factors that affect adoption of computer security practices among college students [dissertation]. Ypsilanti (MI): Eastern Michigan University;2017.
16. Ishikawa K, Ohmichi H, Umesato Y, Terasaki H, Tsukuma H, Iwata N, et al. The guideline of the personal health data structure to secure safety healthcare. The balance between use and protection to satisfy the patients’ needs. Int J Med Inform. 2007; 76(5–6):412–8.
19. Hillel Yaffe Medical Center. In record time: just one month after the cyberattack, Hillel Yaffe has returned to regular activity [Internet]. Hadera, Israel: Hillel Yaffe Medical Center;2021. [cited at 2022 Mar 30]. Available from:
https://hy.health.gov.il/eng/?CategoryID=23&ArticleID=1051
.
20. The Israel Democracy Institute. Eli Horovitz Conference for Society and Economic. The health system’s readiness for crisis scenarios [Internet]. Jerusalem, Israel: The Israel Democracy Institute;2020. [cited at 2022 Mar 30]. Available from:
https://www.idi.org.il/media/15311/health.pdf
.
21. Weenk S. National Cybersecurity Strategies in the Healthcare Industry of Israel and the Netherlands: a comparative overview. Cyber Intell Secur. 2020; 4(1):107–29.
22. Jones CM, McCarthy RV, Halawi L, Mujtaba B. Utilizing the technology acceptance model to assess the employee adoption of information systems security measures. Iss Inf Syst. 2010; 11(1):9–16.
23. Fishbein M, Ajzen I. Predicting and changing behavior: the reasoned action approach. New York (NY): Psychology Press;2011.
24. Rogers RW. A protection motivation theory of fear appeals and attitude change1. J Psychol. 1975; 91(1):93–114.

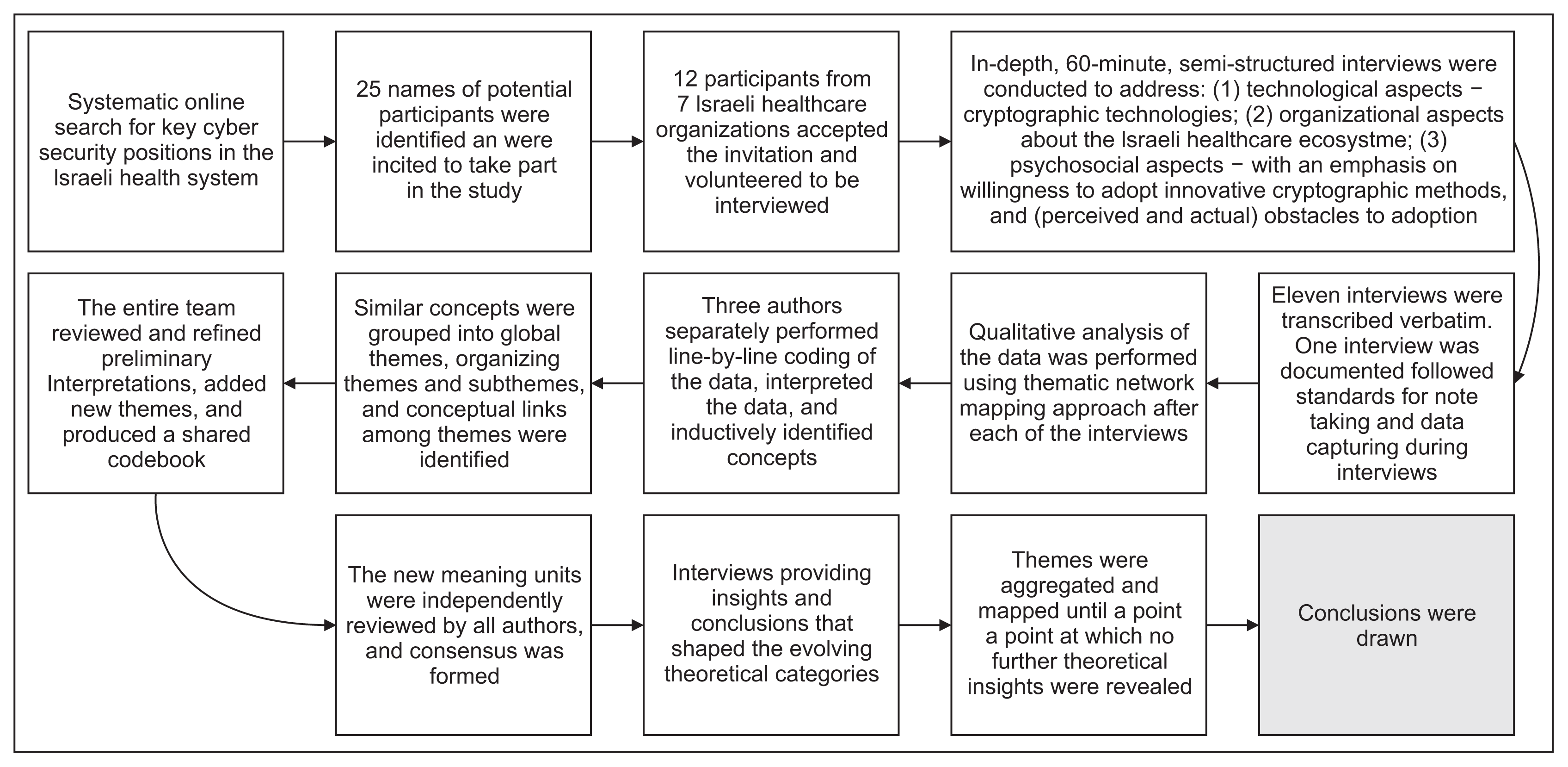
25. Guba EG, Lincoln YS. Epistemological and methodological bases of naturalistic inquiry. ECTJ. 1982; 30(4):233–52.

26. Nowell LS, Norris JM, White DE, Moules NJ. Thematic analysis: striving to meet the trustworthiness criteria. Int J Qual Methods. 2017; 16(1):1609406917733847.
27. Harrell MC, Bradley MA. Data collection methods: semi-structured interviews and focus groups. Santa Monica (CA): Rand National Defense Research Institute;2009.
28. Attride-Stirling J. Thematic networks: an analytic tool for qualitative research. Qual Res. 2001; 1(3):385–405.

29. Charmaz K. Constructing grounded theory: a practical guide through qualitative analysis. Thousand Oaks (CA): Sage Publications;2006.
30. Voigt P, Von dem Bussche A. The EU general data protection regulation (GDPR): a practical guide. Cham, Switzerland: Springer;2017.




 PDF
PDF Citation
Citation Print
Print

 XML Download
XML Download